该报道提出一种“加密式克隆”协议,用以绕开量子“不可克隆定理”的工程瓶颈:未知量子态无法在不测量的情况下复制,而测量会塌缩叠加态。新方案的关键数值约束是“一次性密钥”:可以生成“无限多”份加密副本,但密钥只能使用 1 次,因此最终最多只能解密并观测到 1 份“清晰副本”,从而不违反自然律意义上的不可克隆。研究由加拿大滑铁卢大学 Achim Kempf 与日本九州大学 Koji Yamaguchi 合作,论文发表于 Physical Review Letters,并类比经典一次性密码本(one-time pad)。
协议机理以“成对纠缠+噪声记录”实现:先生成成对的带噪纠缠量子比特,分成用于承载拷贝的“信号比特”和记录噪声的“噪声比特”(充当密钥)。量子电路让待复制量子比特与多个带噪信号比特相互作用,使其量子态被“压印”到这些信号比特上,从而得到多份“加密克隆”。解密时,另一量子电路让选定的 1 个信号比特与“所有”噪声比特交互以抵消噪声并读出信息;该交互会改变噪声比特的状态,使密钥失效,解释了为何只能解密 1 份。作者对比既有克隆方案指出:以往只能得到近似副本,且副本数量越多质量越差;而该方法在理论上可得到质量不随数量衰减的“完美”加密副本。
实证部分强调可行性与鲁棒性:研究团队与 IBM 合作,在其 Heron 处理器上验证该加密方案,展示可生成“大量”加密克隆,并称对硬件缺陷不“过度敏感”。实验还显示克隆不仅复制原量子态,还能保持与源量子比特原先纠缠对象的纠缠关系。潜在应用被量化为“冗余”的引入:可实现量子版云存储(跨地点存多份加密副本)与更稳健的量子通信/传感(以加密量子比特流传输)。更进一步的方向是对加密量子比特进行计算,虽承认开销显著,但可支持“安全冗余计算”。
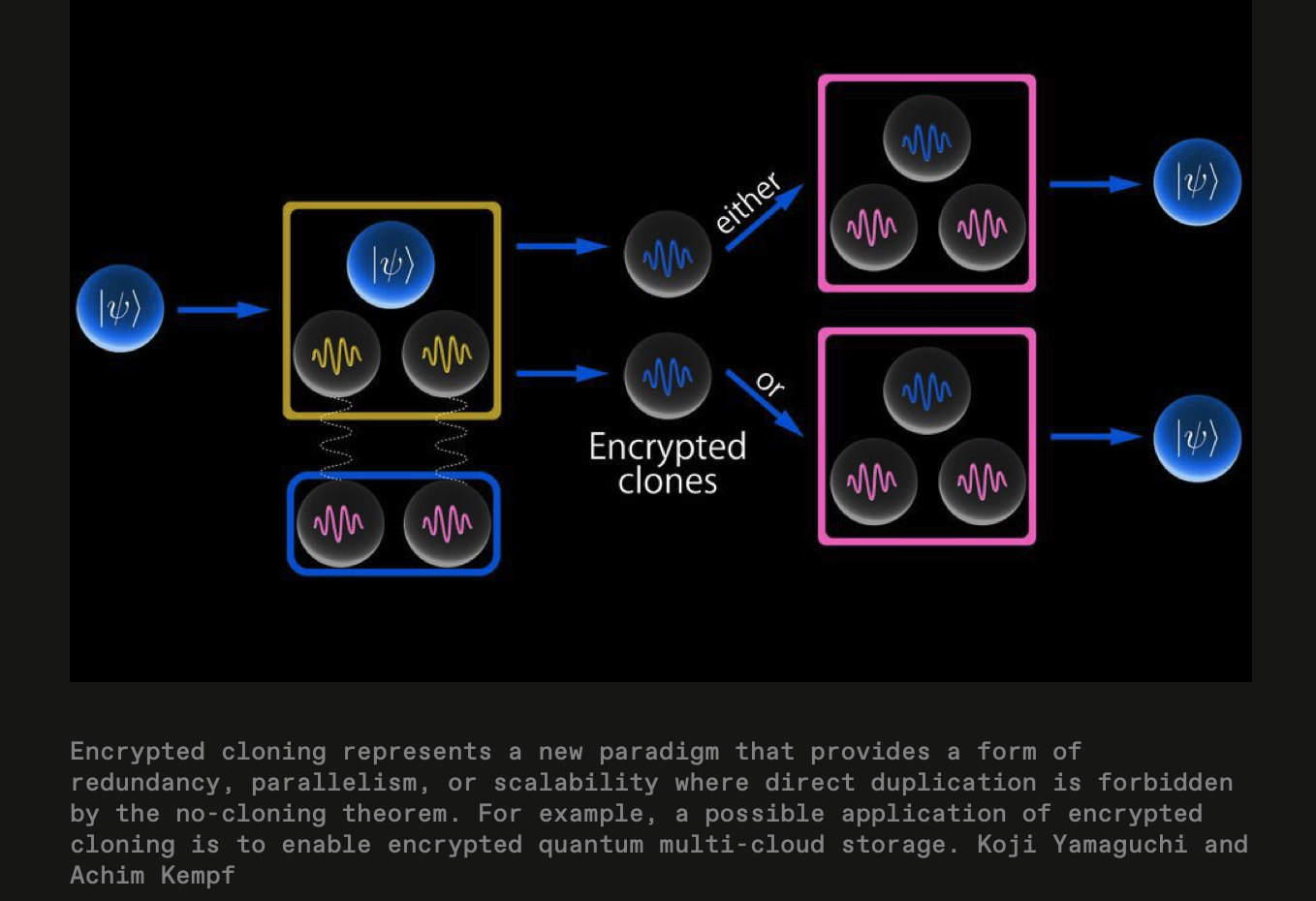
The report describes an “encrypted cloning” protocol that sidesteps the practical obstacle posed by the quantum no-cloning theorem: unknown quantum states cannot be copied without measurement, and measurement collapses superposition. The key numerical constraint is a one-time key: the method can create an “unlimited” number of encrypted copies, but the key works only once, so at most one copy can ever be decrypted and observed as a clear state, preserving the rule that there can be only one readable instance. The work is by Achim Kempf (University of Waterloo) and Koji Yamaguchi (Kyushu University), published in Physical Review Letters, and is explicitly compared to a classical one-time pad.
Mechanistically, the scheme generates pairs of noisy entangled qubits that split into signal qubits (which will hold the clones) and noise qubits (which record the noise and function as the encryption key). A quantum circuit couples the source qubit to many noisy signal qubits, imprinting the source state onto multiple “encrypted” signals. Decryption uses another circuit that makes one chosen signal qubit interact with all of the noise qubits to cancel the noise; that interaction changes the noise qubits’ state, which is why the key can be used only once. The authors contrast this with prior cloning attempts that yield only approximate copies whose quality degrades as more are made, whereas this protocol can, in theory, produce perfect encrypted copies without a quality–quantity tradeoff.
The practical validation cites tests on IBM hardware: in unpublished work with IBM colleagues, the team demonstrated large numbers of encrypted clones on the company’s Heron processor and reported the protocol is not overly sensitive to hardware imperfections. They also found the clones remain entangled with any other qubits the source was linked to, preserving correlations. The application pitch is redundancy: a quantum analogue of cloud storage with multiple encrypted copies in different locations, and more robust quantum communication/sensing via streams of encrypted qubits. A further goal is computation on encrypted qubits, acknowledged to carry significant overhead but enabling “safe redundant computation” in a quantum cloud setting.